In this tutorial, you will learn to generate you private-public ssh key pair, which will allow you to login via SSH using your private key instead of passphrase.
Prerequisite
- Any Linux or *inx (OpenBSD etc…) distro (including WSL)
- SSH installed and enabled
Level of Difficulty: Beginner
Ssh-keygen -m PEM -t rsa -b 4096 If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the -generate-ssh-keys option. The key files are stored in the /.ssh directory unless specified otherwise with the -ssh-dest-key-path option. To generate a key with OpenSSH, use ssh-keygen: ssh-keygen -t rsa -b 4096 This will generate a 4096 bit RSA keypair and (by default) put it in the (homedir)/.ssh/idrsa location, you can change where it goes at the prompt or specify -f in the command line invocation.
Estimate Time to Complete Tutorial: less than 5 mins
What is SSH-KEYGEN
Ssh-keygen is a tool for creating new authentication keypairs for SSH, that can be used for automating logins, single sign-on and for authenticating host.
Create an SSH Key pair
There are several ways to generate a key pair using ssh-keygen.
Below are the different ways you can generate your key pair depending on your needs
Default key par generation
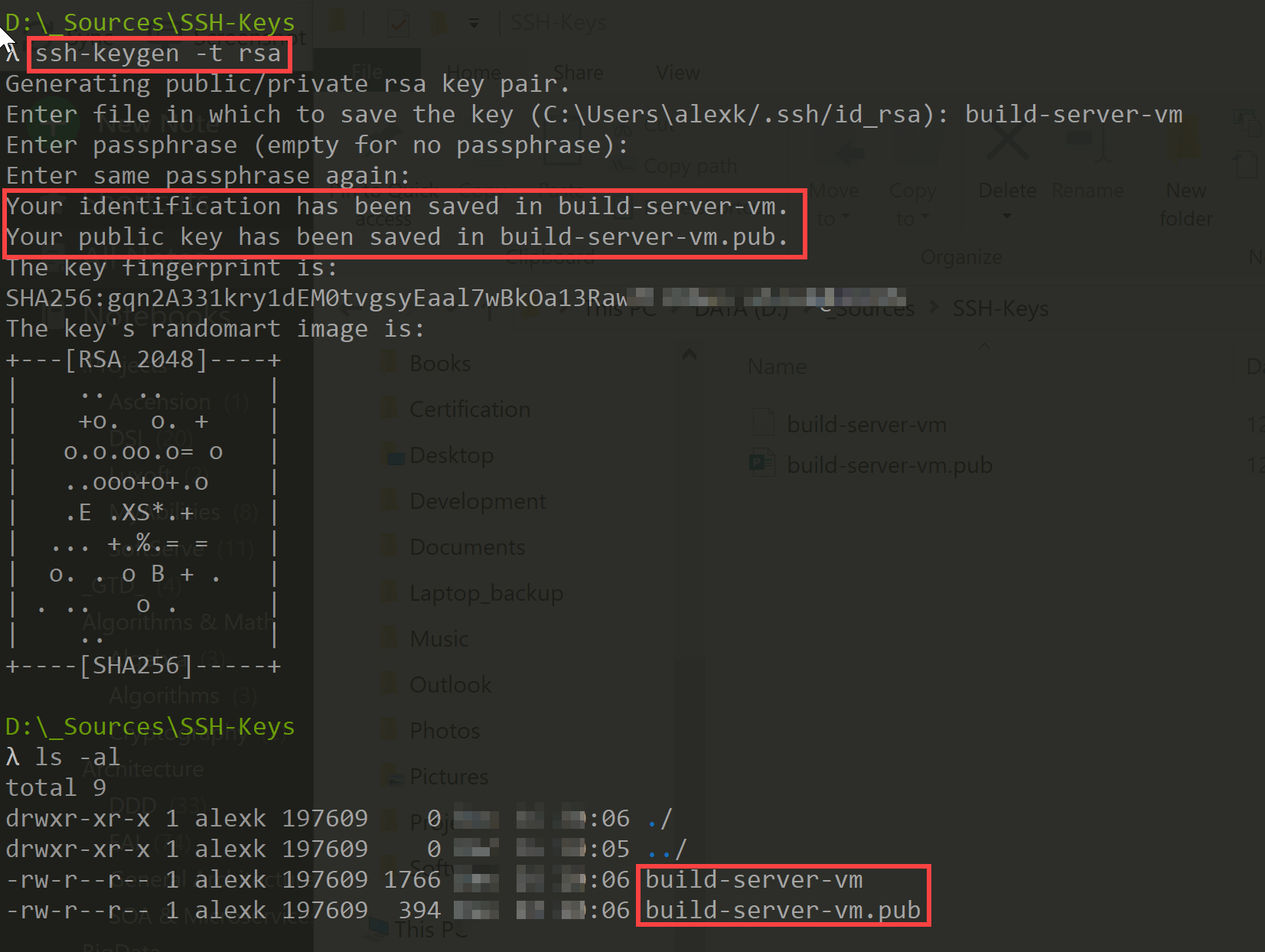
The simplest way to generate a key pair is to run ssh-keygen without arguments.
The tool will ask you where to save the file. If you leave the file path blank it will save it in the default location (in most cases : /home/professor/.ssh/id_rsa).
Next you will be asked for a passphrase (passphrase and password a synonymous in this context). If you leave it blank the private key will not be password protected (for access to critical servers it is highly recommended to password protect the private key, so that even if the key gets stolen, it will require the attack knowing the password in order to use it).
Next you will be asked to confirm the passphrase. (if you left the passphrase blank, leave this blank too)
Generate key par and specify options
For a live environment (or servers with multiplier users, or simply for higher security), it is highly recommended to store the key pair in a different location than the default. You should also use a higher encryption algorithm than the default rsa 2048 (preferable ecdsa). An example of a more secure key pair generation looks as follows:
Do not forget to secure you private key with a very strong password (general rule: a password longer than 14 characters, with atleast a lower case, upper case, numbers, and special characters, generated blindly and store in a secure password vault such as Keepass).
Rsa 4096 Undo Encrypted Files
The different encrypt algorithms of ssh-keygen
Ssh Keygen Rsa 4096 Mac
SSH supports several public key algorithms for authentication keys. These include:
- rsa – an old algorithm based on the difficulty of factoring large numbers. A key size of at least 2048 bits is recommended for RSA; 4096 bits is better. RSA is getting old and significant advances are being made in factoring. Choosing a different algorithm may be advisable. It is quite possible the RSA algorithm will become practically breakable in the foreseeable future. All SSH clients support this algorithm.
- dsa – an old US government Digital Signature Algorithm. It is based on the difficulty of computing discrete logarithms. A key size of 1024 would normally be used with it. DSA in its original form is no longer recommended.
- ecdsa – a new Digital Signature Algorithm standardized by the US government, using elliptic curves. This is probably a good algorithm for current applications. Only three key sizes are supported: 256, 384, and 521 (sic!) bits. We would recommend always using it with 521 bits, since the keys are still small and probably more secure than the smaller keys (even though they should be safe as well). Most SSH clients now support this algorithm.
- ed25519 – this is a new algorithm added in OpenSSH. Support for it in clients is not yet universal. Thus its use in general purpose applications may not yet be advisable.
The algorithm is selected using the -t option and key size using the -b option. The following commands illustrate:
Copying your Public Key to a Server
To use public key authentication, the public key must be copied to a server and installed in an authorized_keys file. This can be conveniently done using the ssh-copy-id tool. Like this:
Once the public key has been configured on the server, the server will allow any connecting user that has the private key to log in. During the login process, the client proves possession of the private key by digitally signing the key exchange.
Key Management Considerations
It is easy to create and configure new SSH keys. In the default configuration, OpenSSH allows any user to configure new keys. The keys are permanent access credentials that remain valid even after the user’s account has been deleted.
In organizations with more than a few dozen users, SSH keys easily accumulate on servers and service accounts over the years. We have seen enterprises with several million keys granting access to their production servers. It only takes one leaked, stolen, or misconfigured key to gain access.
In any larger organization, use of SSH key management solutions is almost necessary. SSH keys should also be moved to root-owned locations with proper provisioning and termination processes. For more information, see how to manage SSH keys. A widely used SSH key management tool for OpenSSH is Universal SSH Key Manager.
Rsa 4096 Encryption
Practically all cybersecurity regulatory frameworks require managing who can access what. SSH keys grant access, and fall under this requirement. This, organizations under compliance mandates are required to implement proper management processes for the keys. NIST IR 7966 is a good starting point.
Conclusion
You should now be able to generate ssh keys, add them to an authorized server and login using the generate private key.
More Tutorials and Utilities
Ssh-keygen -t Rsa 4096
SSH on Windows Subsystem for Linux (WSL)
What is my IP
Enable Windows Subsystem For Linux (WSL)
